

Shift Left Security: Transforming the Software Development Lifecycle
Introduction to Shift Left Security
Shift Left Security refers to the integration of security processes at the earliest stage of the Software Development Life Cycle (SDLC). Traditionally, security testing and verification were conducted in the final phase before the software release, leading to delays in addressing any discovered security issues.
The concept of “shifting left” can be visualized as a line representing the software development cycle, moving from left to right. The shift left approach alters this traditional method by initiating security measures at the beginning of the software development project rather than at the end.
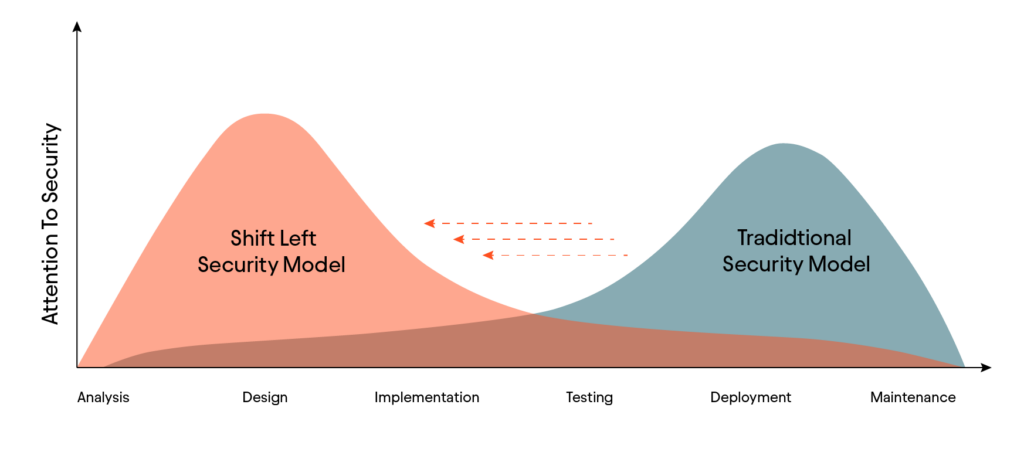
The Necessity of Shift Left Security
Organizations strive for efficiency in their software development projects in the contemporary business environment, aiming to reduce time, cost, and effort. A survey conducted by Shift-Left, involving over 165 developers, AppSec, and DevOps professionals, revealed that 96% of developers feel that the separation between developer and security workflows obstructs productivity.
Addressing security issues as early as possible during the SDLC process and embracing a proactive approach for preventing instead of fixing bugs can save organizations tens fold of costs. Although these figures may vary from one organization to another, it is evident that early intervention saves time and money. The primary benefits of the shift left approach for organizations include:
1. Cost Reduction
2. Effort Minimization
3. Enhancement of Software Code Quality
4. Acceleration of Software Delivery
5. Development of Secure Applications
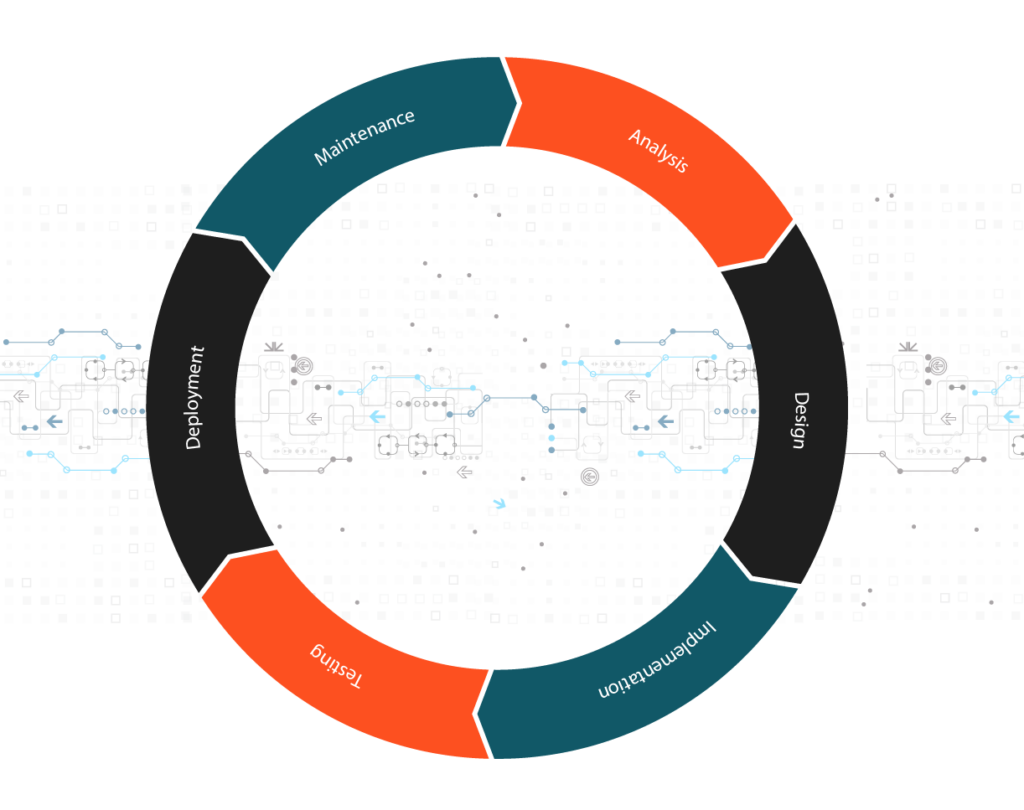
Understanding the Current SDLC
Shift-left security builds on existing practices, so a comprehensive understanding of the current SDLC and coding techniques is vital. This understanding helps identify the necessary steps to be taken during each phase, from planning to production. SDLC comprises the following phases as depicted in the following figure:
Developing a Shift-Left Security Plan
Shifting left in security represents a significant organizational cultural change and requires a well-articulated plan developed by all team leaders involved in the SDLC. Collaboration across various teams is essential, and the program should encompass the following:
1. Objectives of the shift-left strategy
2. Metrics and Key Performance Indicators (KPIs)
3. Defined Responsibilities and Roles
4. Processes, Policies, Procedures, and Standards related to secure SDLC
Embracing Security Automation
The shift left approach can expedite the development process through automation. By defining the steps to be included in the SDLC flow, appropriate tools can be selected for optimal implementation. Some essential steps include:
• Software Composition Analysis (SCA): Identifying vulnerabilities in software components
• Static Application Security Testing (SAST): Analyzing weaknesses in the source code
• Dynamic Application Security Testing (DAST): Analyzing compiled software for flaws
Training Development Teams in Secure Coding
While developers are experts in coding, secure coding practices may not be universally known. Training sessions on secure coding can mitigate weaknesses in the source code and contribute to creating safe, trusted software.
How Oivan Can Assist
Oivan is equipped to facilitate the shift of your security to the left side of the software development process. We offer services such as designing a secure Continuous Integration and Continuous Deployment (CI/CD) pipeline, creating safe coding policies, processes, procedures, and standards, and providing on-demand services for vulnerability assessments, penetration testing, or code reviews. By partnering with Oivan, you can ensure a robust and secure development environment.
By Oivan Cybersecurity Team.
Get In Touch
Want to hear more about shift left security? Let’s talk! Book a free consultation with us. Send us a message for more information.
Cybersecurity Services
"*" indicates required fields